Pegasus Spyware
Abstract
In 2015, Ahmed Mansoor, an internationally known civil rights activist, received two suspicious text messages and sent them to Citizen Lab, a research group, and Lookout, a mobile security company. These groups investigated the text messages and discovered that they contained malicious links that performed a one-click remote iOS jailbreak. This jailbreak used three zero-day vulnerabilities, called “Trident,” to silently compromise the phone before turning it into a remote monitoring device. The spyware, called “Pegasus,” was traced back to an Israeli cyberwar company called the NSO Group which produces spyware for government use. This report examines the technical aspects of the Pegasus spyware as well as the ethical and legal issues surrounding government owned spyware.
Discovery
On August 1st, 2015, a man named Ahmed Mansoor received two suspicious text messages containing a link to an unknown website that supposedly contained secrets about Emiratis being tortured in state prisons. Ahmed Mansoor, who is a well known civil rights activist from the U.A.E., is frequently targeted by spyware and decided to forward the text messages to two organizations: Lookout and Citizen Lab. Lookout is a mobile security company that investigates and helps prevent malware and spyware on both private and business mobile devices. Citizen Lab is a University of Toronto based research group that studies information controls impacting the security of human rights. When Lookout received the text messages sent to Mansoor, they opened the link on a factory-reset iPhone running on iOS 9.3.3 and watched as the spyware opened a blank page in Safari that closed after 10 seconds, silently installing Pegasus onto the phone. Citizen Lab recognized the link from previous research as belonging to a private Israeli spyware company called the NSO Group, linking them to the creation of Pegasus. The NSO Group is a cyber war company that builds spyware to be sold for millions of dollars to governments. They claim that all of their products are used for lawful interception by their customers to “help them combat terror and crime.” Because of the connection to NSO Group, it is assumed that the issuer of the attack was the U.A.E. government, especially considering their previous attacks on Mansoor and their ability to fund a spyware such as Pegasus.
What is Pegasus?
Pegasus is a one-click remote jailbreak that uses three zero-day iOS vulnerabilities called “Trident”. The spyware is all-encompassing, meaning that it can access virtually everything on the target’s phone. This includes text messages, phone calls, location, passwords, emails, and any third party apps on the device. When the malicious link is clicked, the spyware uses Trident to silently install itself and jailbreak the phone, turning it into a remote monitoring device. Pegasus targets iOS 9.3.3 or earlier, but it is important to note that Trident can also affect OS X 10.10 and 10.11, although currently no Pegasus attacks have been found on these operating systems. The spyware is above all else very stealthy, choosing to self-destruct when the phone or its data may be compromised.
Trident
CVE-2016-4657: WebKit Memory Corruption
The first step to installing the Pegasus spyware is to send the victim a link to a malicious webpage. Once the user clicks on the link and navigates to the web page, JavaScript code on the page begins to execute. Normally, regions of raw memory are marked as non-executable, meaning that trying to execute machine code from these regions will cause an error. However, the JavaScript code exploited a vulnerability in WebKit, a framework used in Safari, which allowed the attacker to create a region of memory that is both writable and executable. Once the attacker had this region, he or she could execute arbitrary code and begin the second step of the attack.
CVE-2016-4655: Kernel Information Leak Once the attacker can write and execute code, the next step is to determine the kernel’s location in memory. Many attacks, such as ROP, require the attacker to know where code is located in memory in order to execute them. Kernel Address Space Layout Randomization (KASLR) make these attacks much more difficult by randomizing the location of the kernel in memory each time the phone is turned on.
To bypass KASLR, the attacker exploited a bug that leaked the kernel’s location. Specifically, the bug allowed the attacker to create an invalid OSNumber and read data from the kernel’s stack. OSNumber is a class in the kernel that has two main fields:
-
Value (pointer)
-
Length (in bits)
Normally, OSNumbers only have lengths of 8, 16, 32, or 64 bits. However, a bug in a dictionary deserialization function did not validate the size properly, allowing the attacker to specify a length much longer than the actual OSNumber data. Later, when the kernel read the OSNumber value to return to the user, it would use the invalid length, thus returning the contents of the adjacent memory (Figure 1).
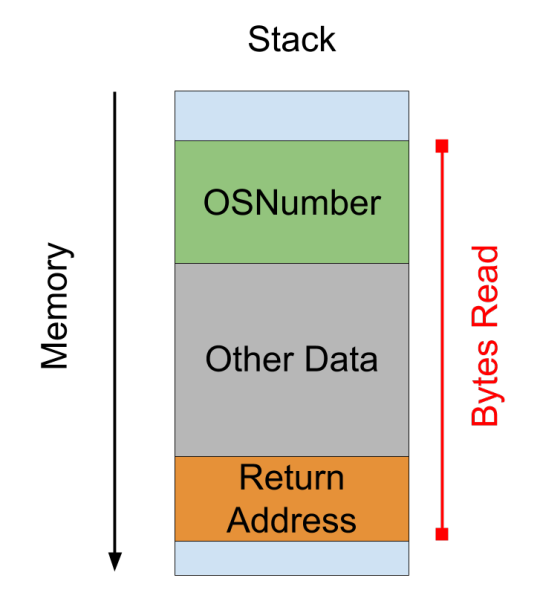
Figure 1
CVE-2016-4656: Kernel Use-After-Free Now that the attacker has the kernel location, the final step is to compromise the kernel. To compromise the kernel, the attacker exploits a use-after-free vulnerability in a dictionary deserialization function. A use-after-free vulnerability is a situation where a program tries to access a memory location that has been freed. Figure 2 walks through how the attacker exploits a use-after-free vulnerability:
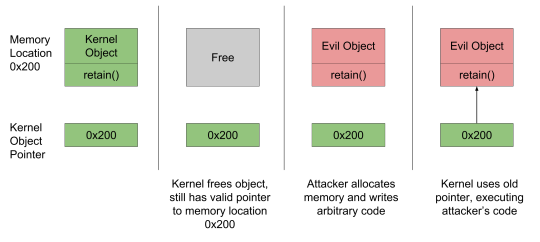
Figure 2
First, the kernel has a valid object and a pointer to that object. Second, the kernel frees the object, but fails to clean up the pointer. Next, the attacker allocates the freed memory with the attack payload. Finally, the kernel accesses the pointer, executing the attacker’s payload.
For this specific exploit, the attacker crafts a specialized dictionary, outlined in Figure 3 that, when deserialized by the kernel, will exploit a use-after-free vulnerability. This dictionary contains three key-value pairs, the first of which has a key of type OSString. When this first element is parsed, an OSString object is created for the key and a pointer to that object is stored in an array. Then, the OSString object is converted into an OSSymbol and then freed. During this conversion, the original pointer is not modified or destroyed.
After the OSString to OSSymbol conversion, the second key-value pair, which contains the attack payload, is deserialized. In the XNU kernel, the heap allocator reallocates the most-recently freed memory locations first. Since OSString objects are 32 bytes in length, the attacker can allocate the recently freed OSString object by making the attack payload 32 bytes in length. This payload overwrites the vtable pointer section of the object, allowing the attacker to specify an alternate vtable.
Finally, the third part of the dictionary is processed. Here, the value is a reference element, meaning that it references the first element of the dictionary. When the kernel processes this element, it will retrieve the original OSString key pointer for the first element, which now points to the attack payload, and call retain(). This call will begin the code-reuse attack, resulting in elevated privileges for the attacker.
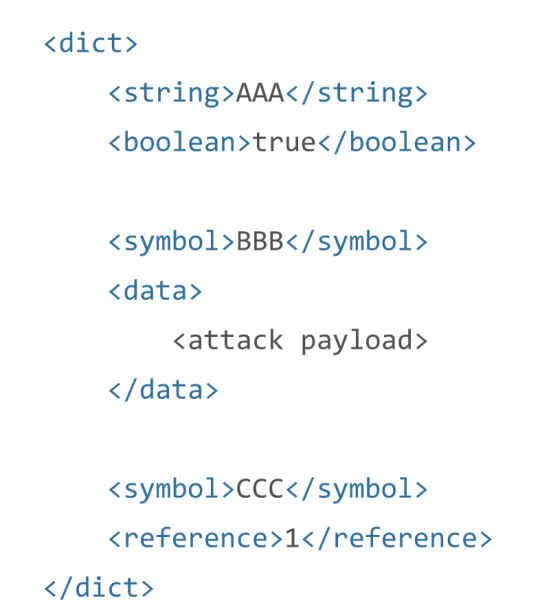
Figure 3
Prevention
In response to the attack on Mansoor, Apple released a patch on August 25th, 2015 for the Trident vulnerabilities affecting iOS as well as OS X. The best way to prevent an attack like Pegasus is to update your devices to the latest available software to obtain any new security patches released by Apple. It is important to note that if your phone currently has Pegasus installed, updating to iOS 9.3.5 or later will not remove the spyware. On another note, you should never backup your data if you believe your phone has been attacked by Pegasus. Doing so may trigger a self-destruct mechanism that wipes any trace of Pegasus from your phone and thus any evidence of a breach. Another way to keep your device secure is to use Lookout’s Mobile Endpoint Security application to detect any new or existing spyware or malware. On a broader scale, Apple has also started a Bug Bounty program that can help find iOS vulnerabilities like Trident.
Ethical Issues
There are a myriad of ethical issues surrounding the Pegasus attack. Many question whether or not it is legal and / or ethical for governments to purchase spyware and secretly use it on their citizens. This question raises the concern of personal privacy and the extent to which governments should be allowed to breach it. Some argue that it is better for governments to utilize existing vulnerabilities like Trident to combat crime in their respective countries, as opposed to creating backdoors that may jeopardize the security of everyone, not just the targets. Whenever a vulnerability is discovered and taken advantage of, there is a possibility of it getting into the wrong hands, whether that is a corrupt government or a lone hacker with malicious motives. Although spyware like Pegasus is intended for the prevention of crime, there is nothing stopping those who control it from using it to target the innocent. As Bill Marczak from Citizen Lab eloquently states:
“The targeting of these activists and dissidents is a taste of what’s to come…what they are facing today will be faced by ordinary users tomorrow.”
_ _
Acknowledgements
This work was done without any outside collaboration.
References
-
https://blog.lookout.com/blog/2016/09/02/pegasus-trident-cio-ciso-what-to-do/
-
https://www.lookout.com/trident-pegasus-enterprise-discovery
-
https://citizenlab.org/2016/08/million-dollar-dissident-iphone-zero-day-nso-group-uae/
-
http://www.businessinsider.com/pegasus-nso-group-iphone-2016-8
-
https://www.nytimes.com/2016/08/26/technology/apple-software-vulnerability-ios-patch.html
-
http://variety.com/2016/digital/news/iphone-hack-pegasus-malware-security-ios-update-1201845700/
-
https://www.wired.com/2016/08/hacking-group-selling-ios-vulnerabilities-state-actors/
-
http://www.imore.com/apple-has-patched-pegasus-malware-heres-what-you-need-know
-
http://sektioneins.de/en/blog/16-09-02-pegasus-ios-kernel-vulnerability-explained.html
-
https://info.lookout.com/rs/051-ESQ-475/images/lookout-pegasus-how-to-tell-impacted.pdf