Operation BugDrop
Abstract:
The CyberX team recently discovered a massive cyber-reconnaissance operation that primarily targets Ukraine’s critical infrastructure, media, and scientific research. The malware is known to remotely control PC microphones to eavesdrop on conversations and captures a range of other sensitive data, such as screenshots, documents, and passwords, then uses Dropbox to exfiltrate said data. According to CyberX, using Dropbox is a clever approach because “Dropbox traffic is typically not blocked or monitored by corporate firewalls”.
BugDrop uses quite a few clever tricks to evade detection, we will look at them in this report and also other technical issues behind this operation.
Superficial Issues Presented in the Media:
Operation Bugdrop got some media coverage, namely from Forbes and Ars Technica. Most media coverage neglects to mention that this is a targeted attack, and instead state that this effects a wide-range of people. BugDrop was also sensationalized because of its ability to eavesdrop on private conversations. Most users can thwart video surveillance simply by covering up their cameras, but short of physically disabling the speakers, victims can’t protect against the virus from recording audio easily.
Additionally, the media presented coverage on potential political motivations behind this attack. Most of the targets are based in Ukraine. However some come from Russia, Saudi Arabia and Austria. Many of the Ukrainian targets are located in Donetsk and Luhansk, which are self-declared separatist states and have even been classified as terrorist organizations by the Ukrainian government. One target is a company that designs remote monitoring systems for oil and gas pipeline infrastructures. Thus, the media identified that seems to be a correlation between the attacked organizations gas pipelines, infrastructure, and counter-terrorism organizations.
Underlying Technical Issues:
Victims are infected through a targeted email phishing attack that contains a malicious Microsoft Word document. The decoy document has in it hidden malicious macros, that, once enabled, runs a harmful Visual Basic script. To get the target to enable macros, a realistic looking dialog box pops up essentially saying: “Attention! The file was created in a newer version of Microsoft Office programs. You must enable macros to correctly display the contents of a document.” If the user complies and enables them, the VB script runs. It extracts the main downloader contained in the decoy document and runs it from the temp folder, essentially changing the .tmp extension to .exe . This is possible because a Microsoft Word document is not a single binary file, but in fact a compressed directory of folders and files. So, not only is it possible to hide extra content within a document, it’s easy. The hard part would be avoiding detection.
Within the dropper are 2 DLL files that, through obfuscation, avoid being detected by AV products. Obfuscation is a process applied to information to intentionally make it difficult to reverse without knowing the algorithm or method used. This contrasts with encryption which keeps everything out in the open except for the key. In this malware, the method of obfuscation is that the DLLs are xor’ed in a special way such that the end result doesn’t look like a normal Portable Executable file loader. Below is a diagram of how the xor’ing happens:
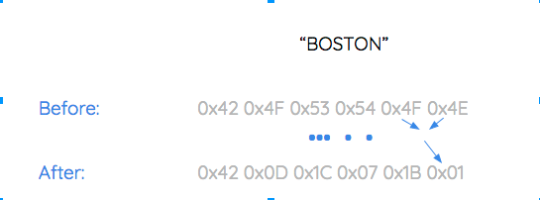
A DLL is a dynamic-link library that contains code and data that can be used by more than one program at the same time. DLL’s are specific to Windows machines.
Now that the dropper is extracted, the main stages of the dropper are executed through the two main DLLs (loadCryptRunner.dll and esmina.dll). After the DLLs are deobfuscated, stage1 comes in place about achieving Persistency. The first DLL is injected into the system through Reflective DLL injection. This technique is an advanced version on the normal DLL injection such that in a normal DLL injection. The dropper will inject the first DLL by calling a specific Windows API functions to force the victim process to load the malware DLL within the victim process. This will provide a mask for the DLL malware to run under the victim process. Using a typical DLL injection makes the injected DLL easily detectable by the host system since it uses Windows API functions. In a reflective type of this attack, the malware DLL is injected to the victim process without using any of Windows API functions. This way it’s very hard for the host system to detect.
Once the first DLL is injected, one of the ways to achieve persistency under Windows is through modifying this registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\drvpath
This key in Windows is responsible for the applications that can auto run when the system restarts or resets. Modifying this key only requires user level permissions, so the malware can change this easily without the need for any administrative privileges. Now that the first stage is done, the malware would load the second DLL for the second stage using a Reflective DLL injection.
After the data stealing plugins are installed and running, they output their data locally to %USERPROFILE%\AppData\Roaming\Media. Within this folder, it is encrypted with a symmetric key block cipher known as Blowfish, using the client ID as the encryption key. Afterwards, the encrypted data is sent to the same Dropbox account where the plugins were downloaded from for organization and retrieval. Once retrieved, the attackers delete the encrypted data from Dropbox and decrypt and analyze the contents of the files on their local devices.
Once the second DLL is injected, it’s responsible for downloading the main module through a hardcoded URL that is stored within the DLL itself. The URL is the following:
windows-problem-reporting.site88.net [Note: Do not visit this malicious site.]
Accessing this URL directly would result in a “404 NOT FOUND” message, so it appears as if downloading the main module requires manual approval, indicating the need for some kind of a handler in the procedure. This assumption is reasonable given how this attack was quite specialized (attack range: ~71 victims). After the approval to download, the main module is loaded into memory also using a Reflective DLL Injection.
Once the main module has been downloaded, it starts its operation by checking for the presence of reverse engineering tools. This ensures that the subsequent steps can not be analyzed and patched easily. It first checks if a debugger is present. A debugger can track the execution of the main module and the associated processes step by step. The checks also determine if a process is running in a virtualized environment, which would isolate the module from affecting the rest of the computer. Additionally, the checks also look for two other programs, ProcessExplorer and Wireshark. ProcessExplorer can be used to identify legitimate processes that contain malware within them that hide as DLLs, and Wireshark can be used to identify malicious traffic that originates on the computer itself. If any of these checks fail, the main module will halt its execution until it is rerun again.
Once these checks have passed, a request is sent to a Dropbox account for the data stealing plugins. The request has an associated client ID with it, which is unique to the host computer. The attacker can associate certain plugins with certain client IDs, in order to steal a particular type of data from a host computer. The data stealing plugins can steal local files, files on external drives, browser info (including passwords), audio from microphones, and any extra details about the client that the hacker wants (ie IP, MAC address).
Thoughts on how this could have been prevented:
Giving how the flow of this malware started by a phishing mail then enabling macros. One main and critical point of entry such as phishing should be avoided and minimized as much as possible. Macros on the other hand also propose a main attacking windows. Despite their usefulness in automating certain aspects of developing Word documents, macros have been shown to be used to install viruses on computers of unsuspecting victims. The main take away to consider to prevent macros attacks is to avoid enabling them on a document that is downloaded from the internet, especially from a suspicious website.
In addition to the above measures, it is possible that this particular attack can be prevented if the anti-Reverse Engineering checks failed. So, for example, if the host computer had a debugger active, ran in a virtualized environment, or had ProcessExplorer or Wireshark running, the checks would not pass and the data stealing plugins would not be downloaded. Although this would not result in total removal of the main module itself, these measures would prevent the data stealing plugins from downloading in the first place. However, implementation of these measures is quite excessive for the average user, and it would not be considered bad security practices if one failed to have a reverse engineering tool at their disposal.
Incentives:
CyberX seems to think the attackers behind BugDrop are backed by substantial resources. According to them “the operation requires a massive back-end infrastructure to store, decrypt and analyze several GB per day of unstructured data that is being captured from its targets. A large team of human analysts is also required to manually sort through captured data and process it manually and/or with Big Data-like analytics”. Although they maintain the attack has “nation-state level capabilities”, CyberX stopped short of attributing the attack to a specific nation-state or group.
As mentioned by the media reports, there is a possibility that there was an effort to destabilize certain key infrastructure related to oil and gas within the Ukrainian separatist states of Donetsk and Luhansk. Although the email associated with the Dropbox account had a Russian domain, there is not sufficient evidence to assume that Russia was involved at all. In fact, it may indicate that a nation was trying to blame the attack on Russia for some reason in order to destabilize the already controversial region in Eastern Europe. However, given the complicated political climate, any further analysis would be entirely speculative.
Acknowledgements:
This work was done without any outside collaboration.
References Used:
http://thehackernews.com/2017/02/ukraine-russia-hacking_20.html
http://www.pymnts.com/news/security-and-risk/2017/new-malware-strain-records-pcs-audio/
http://www.harmonysecurity.com/files/HS-P005_ReflectiveDllInjection.pdf
https://support.office.com/en-us/article/Create-or-run-a-macro-c6b99036-905c-49a6-818a-dfb98b7c3c9c
https://support.microsoft.com/en-us/help/815065/what-is-a-dll
https://askleo.com/whats-the-appdata-roaming-folder/
http://resources.infosecinstitute.com/common-malware-persistence-mechanisms/
https://www.whois.com/whois/site88.net
https://isc.sans.edu/forums/diary/Decoding+Common+XOR+Obfuscation+in+Malicious+Code/13354/